
LDAP/Active Directory Setup |

|

|

|
|
LDAP/Active Directory Setup |

|

|

|
|
|
||
Two options are provided for LDAP/Active Directory authentication: One-step authentication and two-step authentication.
One-step authentication uses the user credentials entered on the application login form to authenticate the user and look up the required user information in the LDAP/AD directory. This option assumes that the user logging in has permission to query the directory structure on their own behalf to authenticate their login.
In two-step authentication (new feature starting with the 7.5.12 release) the system binds using the system account credentials. System account credentials are stored and used to look up the required user information (including the distinguished name) in the LDAP/AD directory for the username entered on the Astra login form. The distinguished name is then used with the password entered on the login form to authenticate the user. (The token for this is in the user lookup filter (%UserName%))
To configure one-step authentication for your institution, perform the following:
1.Click the LDAP Configuration option from the Setup tab.
2.Click Edit to edit the options on the form.
3.Check the box next to "Authenticate via LDAP" to enable LDAP authentication for your institution.
4.If LDAP authentication is enabled, check the box next to "Update Roles From LDAP Groups" to update users’ roles based on their LDAP group membership and mapping rules.
![]() NOTE: If this option is not selected, the user will still be assigned a role when initially created but no role updates will occur in the future should their group membership change. If this option is selected and the user is removed from a group that is mapped to Astra Schedule roles, then the user role will revert to the “Guest” role.
NOTE: If this option is not selected, the user will still be assigned a role when initially created but no role updates will occur in the future should their group membership change. If this option is selected and the user is removed from a group that is mapped to Astra Schedule roles, then the user role will revert to the “Guest” role.
5.Fully Qualified Paths
•Enter a fully qualified path to the LDAP/Active Directory server and root directory that should be searched during authentication.
Multiple paths may be entered to reflect multiple servers or OU’s. Note that specifying multiple servers may decrease authentication performance. The servers are checked in top-down order, so it is recommended that the server with the most potential active users be specified first.
The path is composed of the following elements. Use the following format information and examples to create your path. This format is used anywhere an LDAP path is entered on the LDAP configuration page. (Items in [] are optional.)
LDAP[S]://Host[:Port]/Search DN[/User ID Format]
•Protocol - LDAP or LDAPS (SSL certificate must be installed on the server for LDAPS. Self-signed certificates are supported, so a certificate from one of the trusted certificate authorities is not required for LDAP authentication.)
•Host - Hostname or IP address of LDAP server
•Port - Defaults are 389 for LDAP and 636 for LDAPS
•Search DN - Distinguished name of the directory entry from which to begin the search. To improve performance, this should NOT be the root.
•User ID Format - This is the string used to format the user id used to perform the LDAP bind. Most LDAP systems will use the distinguished name (DN) of the user.
•Because Active Directory does not always use the user id in the CN/DN, the DN may not be able to be constructed from the user id. The user id can be formatted as domain\user id (aais\jsmith) or user id@domain (jsmith@aais.com). There are two variables that can be used to construct the user id used for the LDAP bind.
•{0} is replaced by the user id entered by the user
•{1} is replaced by the Search DN in this path
(The default value is the user id entered by the user on the login or LDAP configuration page.)
•Active Directory Examples:
LDAP://192.168.0.44:389/ou=maincampus,dc=aais,dc=com/{0}@aais.com
LDAP://myldapserver:389/cn=users,dc=aais,dc=com/aais\{0}
•Novell E-Directory Examples:
LDAPS://192.168.0.84:636/ou=maincampus,o=aais.com/cn={0},{1}
LDAPS://myldapserver:636/ou=maincampus,o=aais.com/cn={0}, ou=maincampus,o=aais.com

6.Test LDAP
•You may use the Test LDAP button at any time to test your fully qualified path. To test your information, perform the following:
1.Enter the fully qualified path. The path will be auto-populated if you have already entered it on the LDAP Configuration Info screen.
![]() NOTE: You must remove the user variable portion of the fully qualified path before executing the test. (/{0}@aais.com)
NOTE: You must remove the user variable portion of the fully qualified path before executing the test. (/{0}@aais.com)
2.Enter the LDAP administrator user name and password.
![]() NOTE: The admin user specified here should have permission to search the entire LDAP or Active Directory structure or results may be inconsistent.
NOTE: The admin user specified here should have permission to search the entire LDAP or Active Directory structure or results may be inconsistent.
3.Enter the Search On attribute (directory service attribute that the filtering is performed on (example: sAMAccountName))
4.Enter the Search For attribute (value to be searched for). This field supports wildcards. (examples: student, stud*)
5.Click Run Test.

•The test will provide a list of all attributes found for that object
•If the test process can bind to the LDAP server but no matches are found, then the results window will read “No results were found in...”
•If the test process is not able to bind to the LDAP server, and error message will appear
7.Max. Query Time (seconds) - Enter the maximum amount of time the system should wait on a response to a query of the LDAP server during authentication. This setting is only applicable if Astra Schedule is able to bind to and query the server. If the timeout is activated, then the system responds as if the username or password were incorrect.
8.User Object Class Name - Enter the name of the container that should be searched for users. (defaults to “user”)
This is a required field on the form, but is not used for two step authentication. You may leave this at the default value if using two step authentication.
9.Search User On - Enter the attribute that will contain the value that will be matched to the user login. (defaults to “sAMAccountName”) (Sun One is typically UID)
This is a required field on the form, but is not used for two step authentication. You may leave this at the default value if using two step authentication.
10.First Name Attribute - Enter the attribute that will contain the user’s first name. (defaults to “givenName”)
11.Last Name Attribute - Enter the attribute that will contain the user’s last name. (defaults to “sn”)
12.Email Attribute - Enter the attribute that will contain the user’s email address. (defaults to “mail”)
13.MemberOf Attribute - Enter the attribute that will contain the list of LDAP groups to which the user is a member. (defaults to “memberOf”)
14.Group Object Class Name - Enter the name of the container that should be searched for groups. (defaults to “group”)
This value is only used if you are mapping LDAP groups to Astra Schedule roles and opting to update roles from LDAP Groups thereafter. This can be ignored if not utilizing those features.
15.Group Common Name Attribute - Enter the attribute that will contain the group common name. (defaults to “cn”)
This value is only used if you are mapping LDAP groups to Astra Schedule roles and opting to update roles from LDAP Groups thereafter. This can be ignored if not utilizing those features.

16.Default Guest Role
•The Astra Schedule role that will be granted to a user that is authenticated by LDAP but does not have a role mapped to their group.
17.Group Mapping
•The Group Mapping feature is used to map LDAP/Active Directory groups to Astra Schedule roles. When a user is authenticated, their group membership information is used to determine appropriate permissions. To map groups to roles, perform the following:
1.Click the Add LDAP Group button.

2.Provide the LDAP administrator user name and password.
![]() NOTE: The admin user specified here should have permission to search the entire LDAP or Active Directory structure or results may be inconsistent.
NOTE: The admin user specified here should have permission to search the entire LDAP or Active Directory structure or results may be inconsistent.
3.Enter fully qualified path for the search.
4.Enter the name filter for the search.
5.This field automatically adds wild cards for a partial name search.
6.Click the Find LDAP Groups button.
7.A list of matching groups is returned.
8.Select a group from the list.
9.Click the Save LDAP Group button.
10.A list of all Astra Schedule roles is returned.
11.Place a check in the boxes next to role(s) to which the LDAP group should be mapped.

12.Click the Save button to add the group-to-role association to the list.

13.Repeat as needed.
14.You may expand individual groups on list page to review the association.
18.Select a Default Guest Role from the drop-down list. This is the Astra Schedule role that will be granted to a user that is authenticated by LDAP but does not have a role mapped to their group.
19.Click Save to save your configuration changes.
To configure two-step authentication for your institution, perform the following:
1.Click the LDAP Configuration option from the Setup tab.
2.Click Edit to edit the options on the form.
3.Check the box next to "Authenticate via LDAP" to enable LDAP authentication for your institution.
4.If LDAP authentication is enabled, check the box next to "Update Roles From LDAP Groups" to update users’ roles based on their LDAP group membership and mapping rules.
![]() NOTE: If this option is not selected, the user will still be assigned a role when initially created but no role updates will occur in the future should their group membership change. If this option is selected and the user is removed from a group that is mapped to Astra Schedule roles, then the user role will revert to the “Guest” role.
NOTE: If this option is not selected, the user will still be assigned a role when initially created but no role updates will occur in the future should their group membership change. If this option is selected and the user is removed from a group that is mapped to Astra Schedule roles, then the user role will revert to the “Guest” role.
5.Check the box next to “Use Two Step LDAP Authentication”.
The form section “Two Step Authentication Settings” will appear.
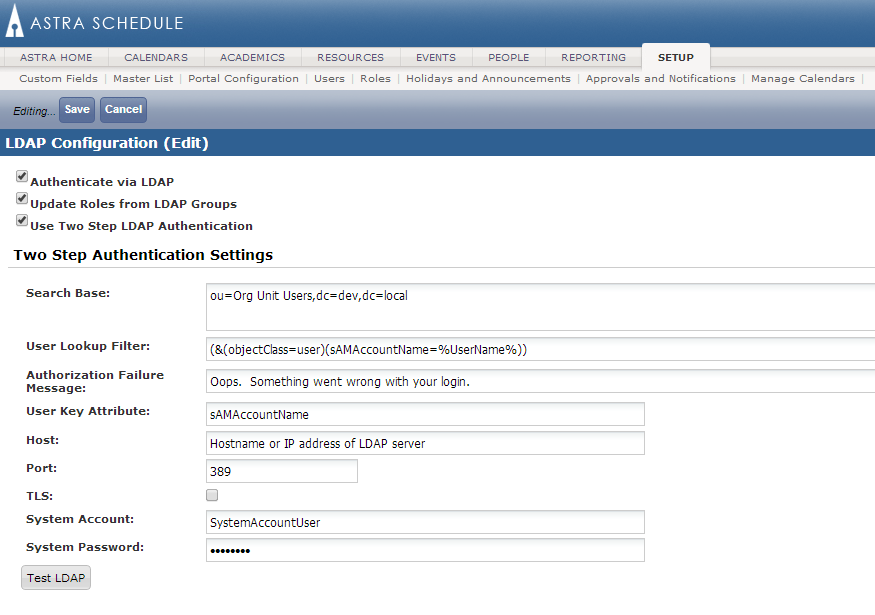
6.Enter the following information for Two Step Authentication Settings:
•Search Base
This is the distinguished name of the directory entry from which to begin the search.
Format Example: ou=Org Unit Users,dc=dev,dc=local
•User Lookup Filter
This specifies the filter parameters to be applied during LDAP directory search.
Example: (&(objectClass=user)(sAMAccountName=%UserName%)), or uid=%UserName%
•Authorization Failure Message
Optionally, enter text that is displayed if the user is not found in the LDAP search.
If no message is entered here, the Astra Schedule standard incorrect user name or password message is displayed.
•User Key Attribute (optional)
Astra Schedule use this LDAP attribute as the key value against which to match LDAP users to Astra Schedule users to determine if they exist already.
When users are created this value is stored as part of the Astra Schedule user record and used during lookup going forward.
A typical example might be “sAMAccountName” for Active Directory.
The user key attribute is displayed on the user form in Astra Schedule.
•Host
The Hostname or IP address of LDAP server.
•Port
The port on which to communicate on LDAP server.
Standard ports are 389 for LDAP and 636 for LDAPS.
•System Account
The distinguished name of the account used to look up the user. It is not assumed that this account is in the search base.
•System Password
The password for system account.
This value is stored encrypted in the database.
•SSL
Check this box if using a secure connection.
To use this option, you must have an SSL certificate installed on the LDAP server.
7.Test LDAP
You may use the Test LDAP button at any time to test your two step authentication. To test your information, perform the following:
1.Enter a test user name and password.
2.Click Run Test.
3.The Response box will indicate whether the user was authenticated or if there was a problem encountered.

8.Configure Shared Settings as outlined above.
9.Configure Group Mapping as outlined above.
10.Click Save to save your configuration changes.